Single Sign-On using SAML
SAML Single Sing-On Configuration
To configure SAML Single Sign-On, you will need to get some details from your Identity Provider - IdP.
A couple of things to notice:
- In the IdP configuration, your LiquidFiles SAML Login URL is: https://your_public_url/saml/init
- In the IdP configuration, your LiquidFiles SAML Consumer URL is: https://your_public_url/saml/consume
- If your IdP wants a metadata URL, you can set that to: https://your_public_url/saml/metadata.xml
- The SAML NameID needs to be set to Email. The LiquidFiles system requires the email to be unique.
- If you set User.FirstName and User.LastName attributes, they will be used to set the users name automatically. This is not required.
- The IdP Login URL is where the browser is redirected when the user clicks on the SSO Login button.
- If the IdP Logout URL is configured, this is where the user will be redirected when the user clicks on the Logout button.
- Authentication of the Identity Provider (IdP) happens with the Certificate Fingerprint from the IdP's certificate.
- The Name Identifier Format and Authn Contexts does not normally need to be changed.
Setting LiquidFiles Group when authenticating with SAML
In Admin → Groups, you can set the default group for users authenticating with SSO. This defaults to the Local Users group.
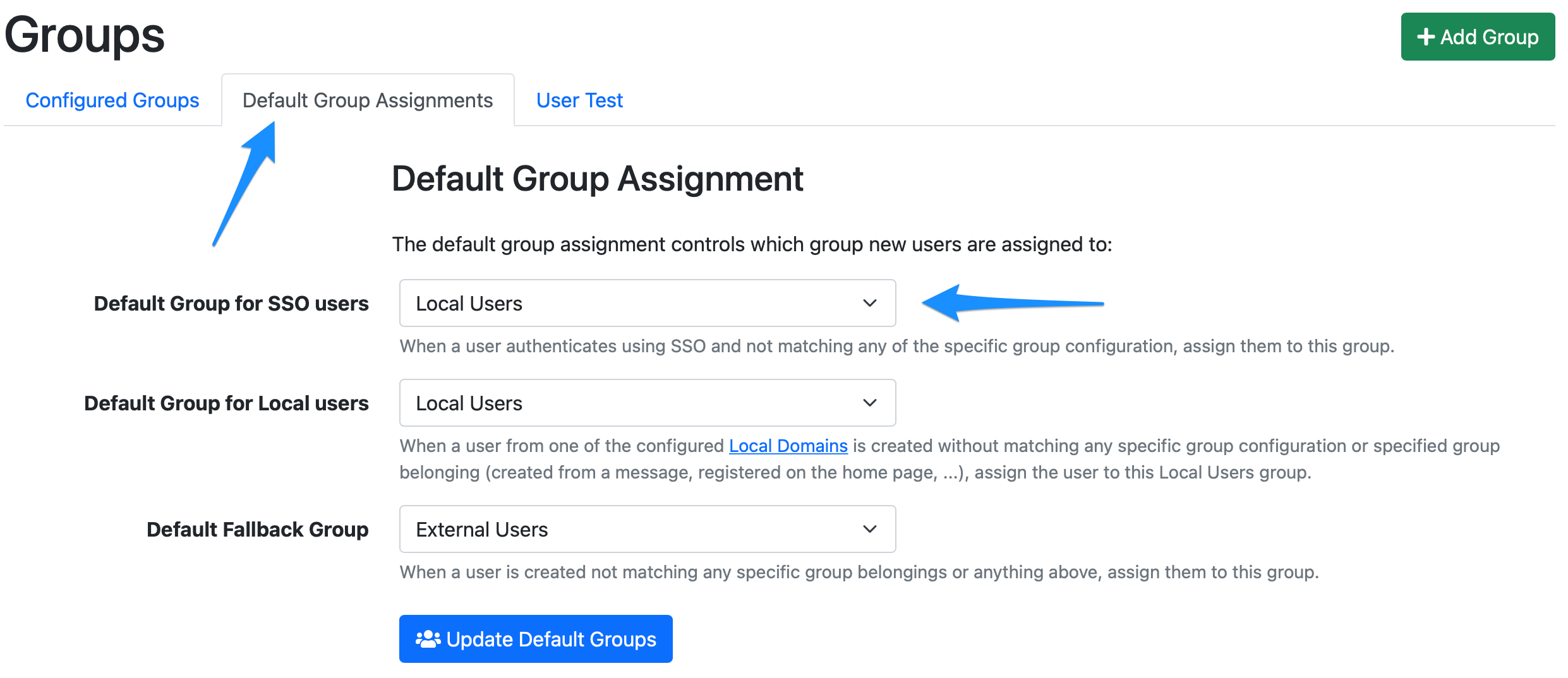
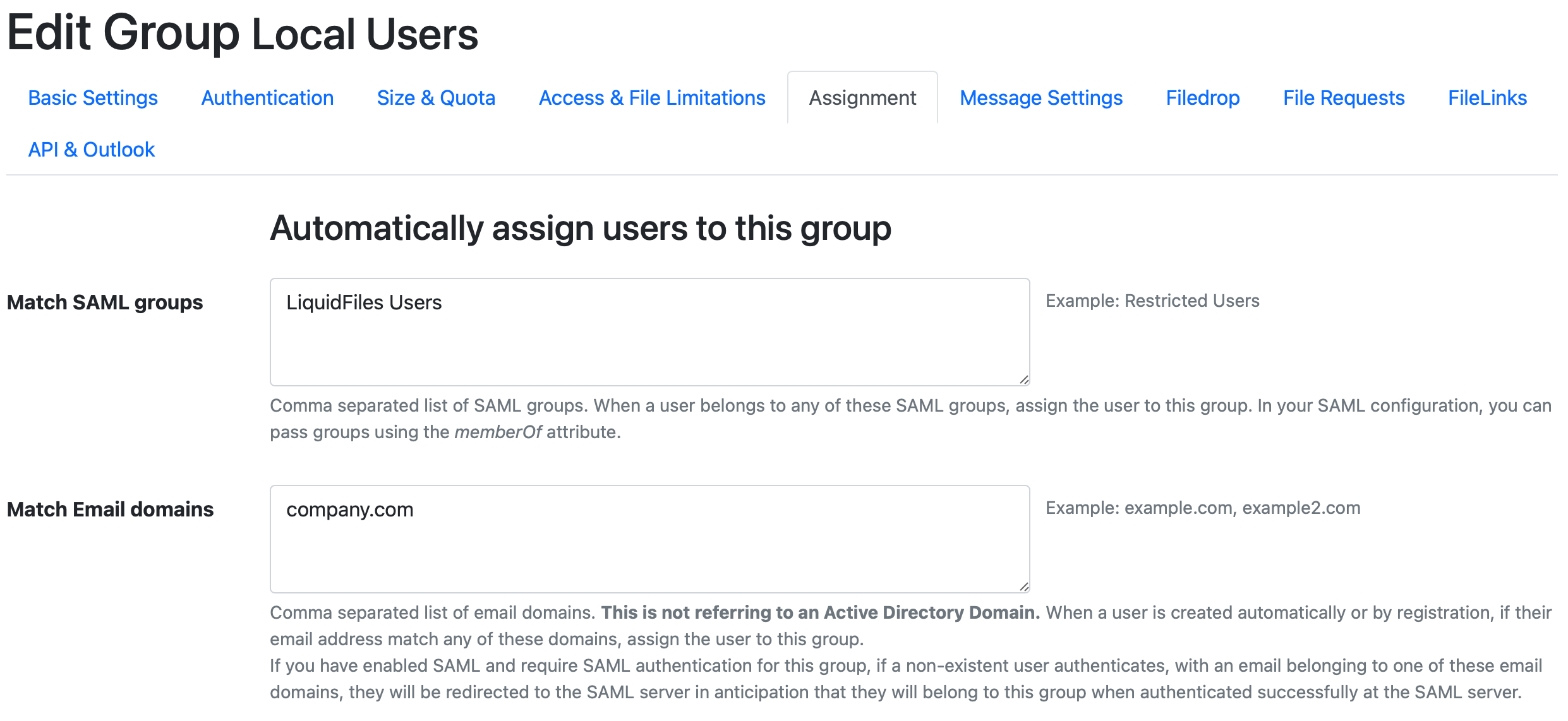
You can also assign users to other groups than the default group by assigning the "memberOf" attribute in your SAML server. Please refer to your SAML server documentation for instructions how to assign custom attributes. When you've set the memberOf attribute to something in the SAML server, you can match the memberOf attribute to a list of groups in LiquidFiles. In the example below, if the SAML server sends an attribute memberOf=LiquidFiles Users, this will be matched to this group (the Local Users group):
Looking up Users in LDAP
If you also have LDAP configured, LiquidFiles will attempt to look up the user in LDAP with authenticting with SAML as well. Since SAML is not a lookup protocol, there are definite benefits to using LDAP together with SAML to lookup users.
If the user is found in LDAP, the name and group attributes will be used to set the name and LiquidFiles group same as when a user is authenticated with LDAP.
Force SAML authentication
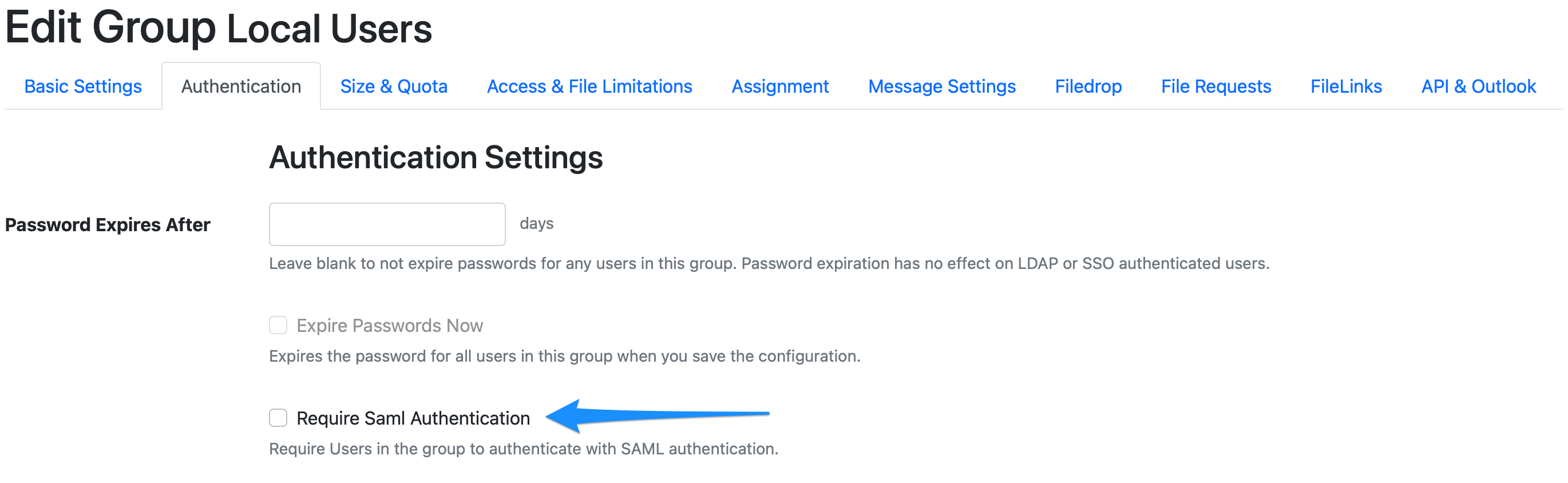
You can force users to use SAML on a per group basis if you want. If you edit the group you want to force SAML authentication for in Admin → Groups, and go to the Authentication Tab, you will see the following:
It is also recommended to add your local domains in the "Match Email Domains" configuration in the assignment tab:

With these configurations, what will happen when the user authenticates is:
- If he user account exist and the user is a member of a group that Requires SAML, it doesn't matter whatever the password the user enters, once the email matches the user account and the user is required to use SAML, LiquidFiles will redirect the user to the SAML server to complete the authentication.
- If the user account does not exist but the email matches the "Match Email Domains", the user is redirected to the SAML server to complete the authentication.
Automatic Login of users using SAML
In the SAML configuration (Admin → Configuration → SSO SAML2), you can add networks that you wish to always authenticate with SAML:
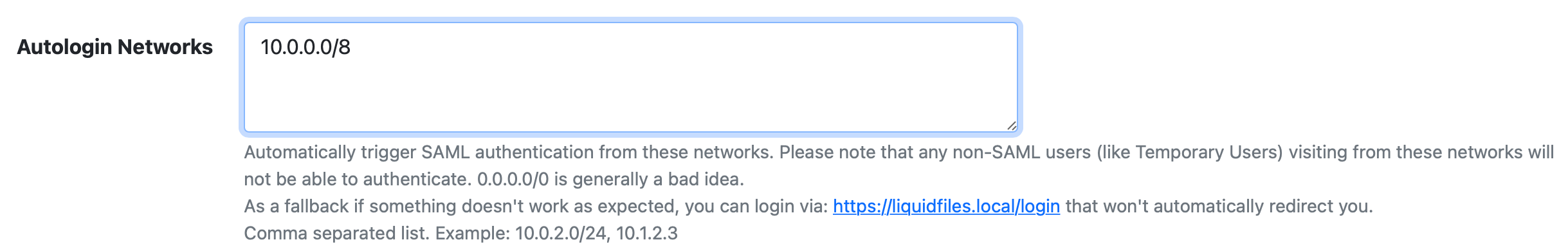
With the setting above, any user that connects with an IP Address in the network 10.0.0.0/8, the browser will automatically be redireced to the the SAML server.
If something goes wrong, and you can't authenticate after making the change above, you can use /login as a safety net. I.e. if your Public URL is https://liquidfiles.company.com, the safeguard login URL would be: https://liquidfiles.company.com/login.
We have seen companies setting 0.0.0.0/0, thinking that "well, we want everyone to always use SAML" but please note that this will stop any form of External User authentication to work, as everyone will always be redirected to the SAML server. If you set the autologin networks to 0.0.0.0/0, you will have to configure all external users in your SAML server as well, which is probably not what you want.
Set this to your internal network ranges and things will work well and as expected.
OneLogin Example
In this example, we're using the Onelogin.com test login.
In the Onelogin configuration, search for test and select the "OneLogin SAML Test (IdP w/attr)"
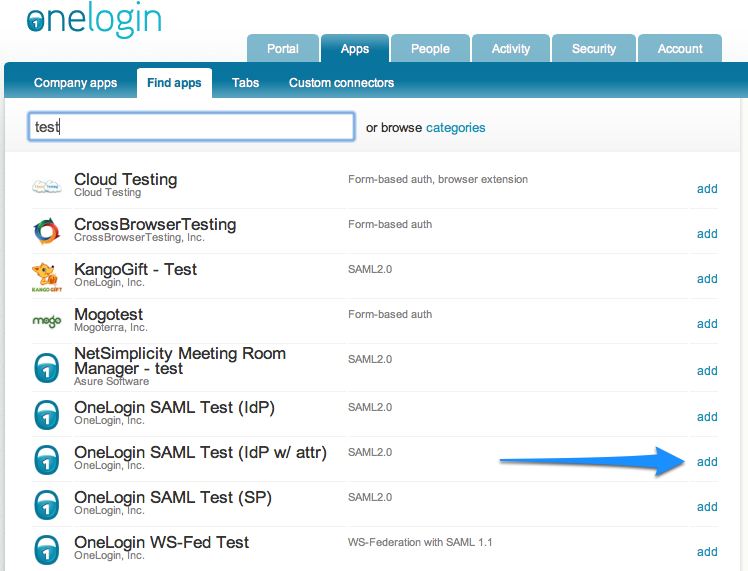
When you've added the test system, add the following configuration:
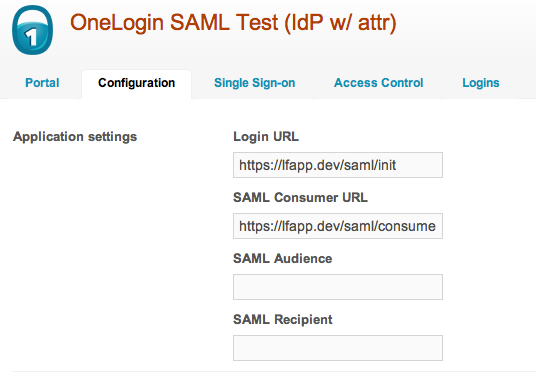
https://lfapp.dev is the base URL for your LiquidFiles system in the screenshot above.
On the Single Sign-on, tab, please configure as following:
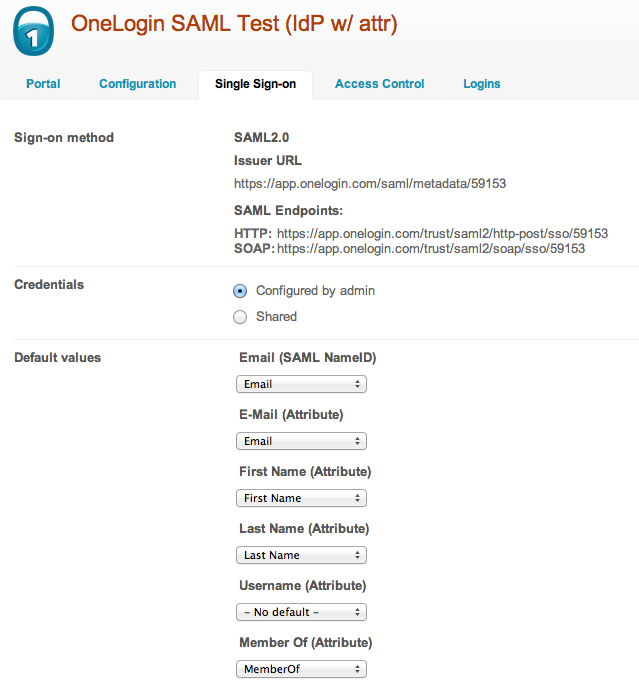
The important setting is SAML NameID which needs to set to "Email".
The other attributes will enable First and Last Name to be added when users are created from logins.
On your LiquidFiles system please configure Admin → Single Sign-On as folllows:
- Idp Login URL: https://app.onelogin.com/saml/signon/59153
- Idp Logout URL: https://app.onelogin.com/client/apps
- Idp Cert Fingerprint: BB:B4:C7:85:55:ED:7B:2B:19:83:EF:F0:32:4A:B6:CC:54:3A:FA:3F
- Name Identifier Format: default
- Authn Context: default
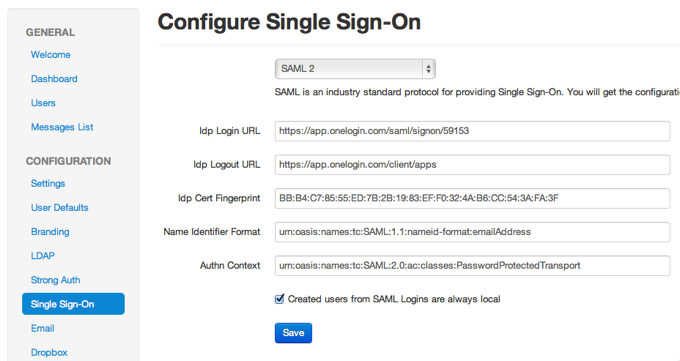
This will enable login either from the OneLogin portal or from the LiquidFiles front page using the SSO Login button:

Microsoft ADFS configuration
A common SAML identity provider in enterprises is Microsoft ADFS. In order to make ADFS work with LiquidFiles, please continue reading this articles:
