Troubleshooting Certificate Chain Issues
Background
If you go to Admin → System → Certificate, you can see the system Certificate Chain for your system. Here's an example:
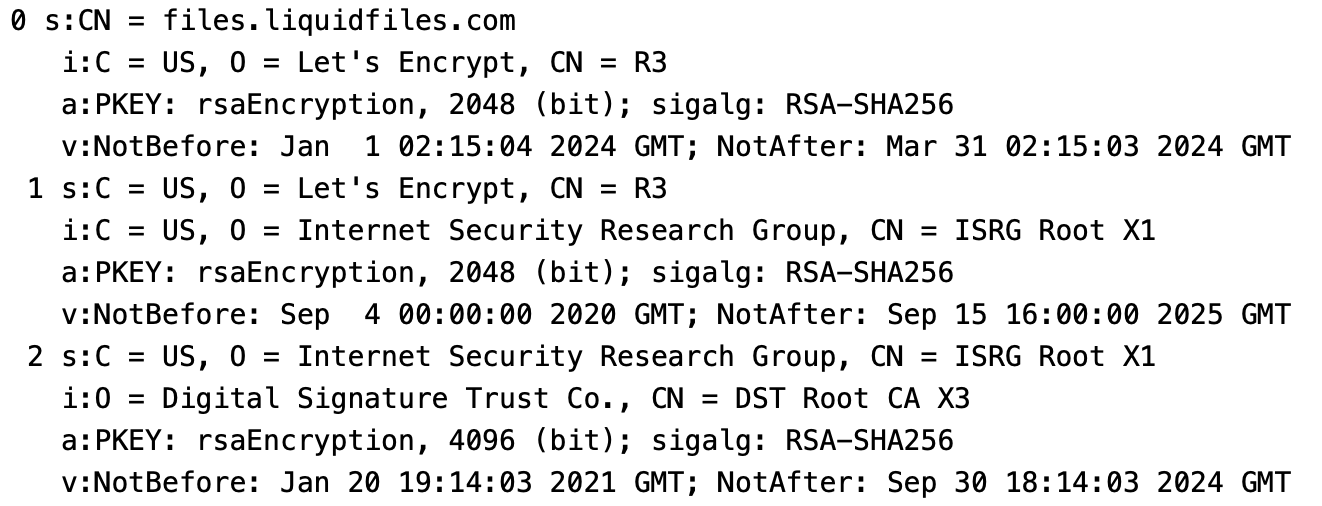
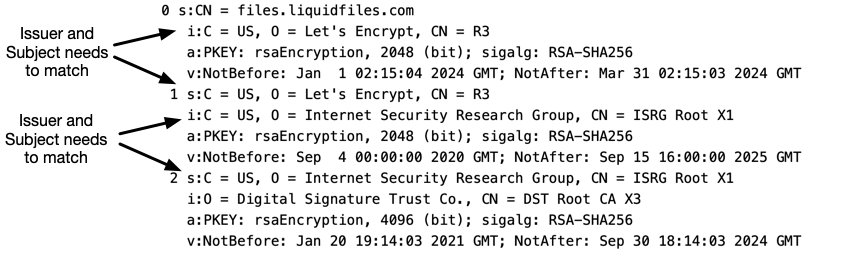
The Certificate Chain is numbered 0, 1, 2, ... Each Certificate has a Subject (who the Certificate is for), and an Issuer (who signed this Certificate). In this Certificate Chain output the Subject is prefixed with a s: and the Issuer is prefixed with an i:. Looking at the top, Certificate 0 is the first certificate and the Subject of Certificate 0 needs to match your Public Hostname (files.liquidfiles.com in this example). If we then look at the last Certificate (number 2), we can see:
s:C = US, O = Internet Security Research Group, CN = ISRG Root X1 i:O = Digital Signature Trust Co., CN = DST Root CA X3
The Last Certificate Issuer is then O = Digital Signature Trust Co., CN = DST Root CA X3. This is called a root certificate. Root certificates are universally trusted and stored in every browser. Since they are universally trusted, it would be extremely annoying if any of those would get compromised. The way this is solved is that these root certificates are stored offline so they are very hard to compromise. This in turn also would make them extremely annoying to use because they cannot be easily used to sign other certificates.
The solution to this problem is Intermediate Certificates. I.e. once every few years Certificate Authorites creates a new Intermediate Certificate and get them signed by an offline root certificate. Using this Intermediate Certificate, they can sign other certificates in a much simpler way and should this certificate get compromised it's not as big of a deal as if a root certificate would get compromised.
In your browser, only the root certificates are stored meaning that when the web server is sending its certificate, it also needs to send any intermediate certificate required. In plain English this would the equivalent of "here's my certificate and here's how you can verify that this certificate is valid", back to a certificate that is signed by one of the trusted root certificates.
This list of certificates sent is called a Certificate Chain, i.e. a Chain of Certificates that link your server's Certificate and one of the Root certificates through one or several Intermediate Certificates.
If we look again at the Certificate Chain above and extract just the Subject and Issuers, we get:
0 s:CN = files.liquidfiles.com i:C = US, O = Let's Encrypt, CN = R3 1 s:C = US, O = Let's Encrypt, CN = R3 i:C = US, O = Internet Security Research Group, CN = ISRG Root X1 2 s:C = US, O = Internet Security Research Group, CN = ISRG Root X1 i:O = Digital Signature Trust Co., CN = DST Root CA X3
For a Certificate Chain to be complete they need to be installed in the correct order so that the Issuer (i:) of certificate 0 matches the Subject (s:) of certificate 1, and the Issuer for certificate 1 matches the Subject for Certificate 2, and so on.
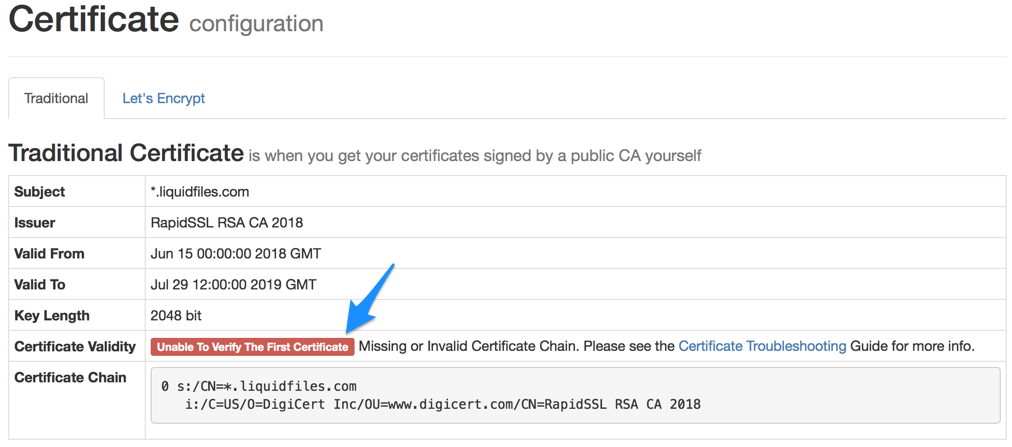
If there's there's no certificate chain installed or the certificate chain is incomplete you will see an error message similar to the following.
Where to get the Certificate Chain Certificate
The Certificate Chain comes from your Certificate Authority. They should have sent you the relevant Certificate Chain when they sent the certificate. If they didn't, you can reach out to your Certificate Authority support and have them send their Certificate Chain. Often you can also find the Certificate Chain with a simple web search along the lines of "DigiCert Certificate Chain", if your Certificate Authority is DigiCert.
