How Certificates work General Information
This section covers general information on certificates. This is mainly if you want to understand the background of how it all hangs together. It is not specifically related to LiquidFiles and you don't need to read this if you only want to install a certificate and get going.
With all certificates, regardless of if they are used on the LiquidFiles appliance or in any other application that uses certificates, they all work in the same way.
The first thing we have to understand is the relationship between the private key, the certificate signing request (CSR) and the Certificate. The relationship between them works like this:
We begin by generating a key. From the key we generate a CSR, and from the CSR we generate the certificate. Also, please note that the arrows are one way from the key through to the certificate. It's not possible, and the security of the entire Internet would fall to pieces if it was possible, to calculate or derive or by any means get hold of the key from the certificate. This also mean that if you loose the key, you will need to generate a new certificate. There is no way around that.
Key: The key is the first things that needs to be generated. The key is what has the key length. Often we refer to a certificate having a key length like 2048 bits. In reality it's actually the key that has the key length. In the LiquidFiles appliance, 2048 bit keys are used as default, but you can install a key and certificate of other lengths if required.
CSR: CSR, or Certificate Signing Request, is what gets sent to the Certificate Authority (CA). We generate the CSR from the key, and we add attributes to the CSR. The most important attribute is the CN or Common Name. The CN needs to match the hostname of the appliance. If the hostname is liquidfiles.company.com, the CSR needs to have a CN=liquidfiles.company.com. It's also possible to use a wildcard certificate. A wildcard certificate will have a CN=*.company.com. The most important thing is that that the CN matches the hostname in the URL or you will get a certificate warning.
Certificate: From the CSR we generate a Certificate by signing the CSR with a private key. If we sign the CSR with it's own key, we call the Certificate a self-signed certificate. For production systems, it's recommended to send the CSR to a public CA and have them sign the CSR. Wikipedia has a list of common Certificate Authorities.
Understanding the Certificate Chain / Intermediate Certificates
It's very common that CA's require intermediate certificates, sometimes also called subordinate certificates or the certificate chain. In order to validate the certificate, the browser needs to verify the server certificate by matching it's signature against one of the known public CA's that exist in your browser. For instance, in Internet Explorer, you can go to Internet Options → Content → Publishers, and you will see the list of trusted Certificates:
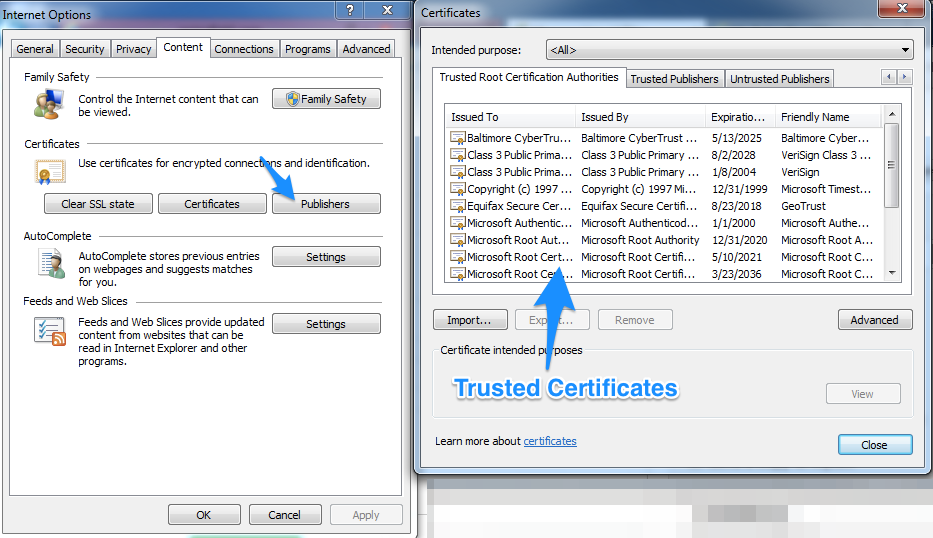
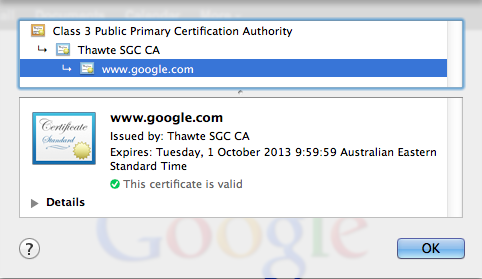
With intermediate certificates, what's happened is that the CA's certificate is not known and trusted, but they have in turn got their certificate signed by one of the known and trusted CA's. If we look at https://www.google.com as an example, by clicking on the security info section when browsing there, you will see something like this:
Or to get another, more detailed view, we can use OpenSSL to connect from the command line, like this:
% openssl s_client -connect www.google.com:443
CONNECTED(00000003)
depth=1 /C=ZA/O=Thawte Consulting (Pty) Ltd./CN=Thawte SGC CA
verify error:num=20:unable to get local issuer certificate
verify return:0
---
Certificate chain
0 s:/C=US/ST=California/L=Mountain View/O=Google Inc/CN=www.google.com
i:/C=ZA/O=Thawte Consulting (Pty) Ltd./CN=Thawte SGC CA
1 s:/C=ZA/O=Thawte Consulting (Pty) Ltd./CN=Thawte SGC CA
i:/C=US/O=VeriSign, Inc./OU=Class 3 Public Primary Certification Authority
---
...In this case the certificate for www.google.com has been signed by Thawte SGC CA, which is not trusted (it is not listed in the browsers list of certificates like in the screenshot above). But the Thawte SGC CA has in turn been signed by "Class 3 Public Primary Certificate Authority" which is actually the second certificate listed in the screenshot from Internet Explorer above. And since we trust "Class 3 Public Primary Certificate Authority" we will also trust "Thawte SGC CA", and since we now trust "Thawte SGC CA" we will also trust that "www.google.com" is secured by the certificate signed by "Thawte SGC CA".
Example Formats
Example Key (so that you can see the format, this is not actually useable):
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAoeW0E0oYUup8JR7ghKi2rkiIpXyNmVPl0A00kffwyWI7YuCS
zsLxBdIxZkPkar/XVT+GD+RJXLCrfUd9t4ZuwWph4wKJK6rulqyRBIHtkrx1XYDH
3r6DXK+Ivw23tkeZmoIo2vq6zHAWsJs5NTOeuto7Tv03nHjGfZvQXWL5hLKkiBjc
fF2VNbvoI61vjKx10vzTqW0qt6CAQe9l9eQVxfDnrl4z67mbt3Nx2KpbiruyBSbd
0FxDokex5mfcC6foVblxBtLQaUA3mFtSSflQN81UyTmZWTkNTPVgUw7CuCBajzFe
3Y1wFsh+fha85yB7Z4MY2z29Mw/v4swLb6WOQwIDAQABAoIBACKomCpg/GATzsvr
lkkQDTu2T3qN9YpTialGinCNUcDrBKegSA13cj26x9SKyEWKGEEpvjt8ta/gKnZB
bcpyPxes/JOqoU714uniu5Dpd8CoE8AWp7MpudmHwpCUETY2kc2f+7sVXhQSEulv
8YlQKbT6ryOz1cnrmSKezraPT7d2Z8p18ayjsrfBlC3sksULwKZWz0iDxMtTORTv
93HdJUw5AiFU/d+i+nQAQkhgRBICkl+j/q3jpVMJerDT2jVWOWgaKGULoHzAQgEs
ce4/TCos6vmKRIHAWyIcHCUPW5pd3b8JkMcAmyfywkvWNNYuei4eNJWLCjbMAg59
H2qcJDECgYEA0a5t2zD1P6UrD0uCe27gpft7H5B9eS74VGCmgcIK6rjTX4NfEQkC
fLfKkr9ru5ccUCGlBpDgecFk05KIuymXIO53wZo7rpM6CuiU7vTLktDvTDVoLAmh
gxJ2NtGsGTHZNaUVTO31kg0ILO8YZe6bRPprfWuNlLW0WXULD92efU8CgYEAxakQ
WCNGxa6Ozfp+gqp3z12hDt5PGXJSn7TjzFbMTSW+IdWxBM3ArkDS1WE8WqVekDsx
lhwURYqjVraTbC7y6fTbts9zOzp59CtChJC/7JjhOVLyaoAmEP1Pt16nJdyqxMZb
3RVWpqrxgcqv8KL+JQIM8DbysJNunxrkh2F/6s0CgYBE4XEzNUULkF2x25NUqxrf
S9qphtTBL33ichGgxLbDXs4JLWXYecY4ZEQGqx1f9YcWh8bnfkZPmQlfO17xZPtB
lTUAA4OhmLnThY4PZZlOdJZ3yX+cH9nP7gupfH11lVuOdNmnePBX9zH9WNoB+j1F
jqIrBF7xQDOrw3hL0PjUnwKBgQCNneq661NqkP158K4xmkdLCE87ouXTWoh+KpFH
tyybXZ5TCZLR2UTi1Ej6XrdqTq9o8TA+15FinckXeKo5SY37N9cvrIRn/CaiXVhE
OJ15u7MqahaLXZNoesVhoOxrASZM472vsfkqYrG0B291HqKuC0EP3p6VCpyoXBE+
Ogn3RQKBgQCAbdY6KqkQYKtL0+qBbI95Q4ZG0DE9oLwdQLEezo6ituG5v9WeAshG
y5Qv94tSZQGM59wqeIY2bHeCiYXZdtItIfbx9zM4Ka4VjIYMObK+/yxMb08pFd0/
bx28mhUd06hLNxTzOYRyJ0RFpUjSvEbBaTg6K4pIYOh84NfRNGJcvw==
-----END RSA PRIVATE KEY-----Example CSR (so that you can see the format, this is not actually useable):
-----BEGIN CERTIFICATE REQUEST-----
MIICWzCCAUMCAQAwFjEUMBIGA1UEAxMLZG9udC51c2UubWUwggEiMA0GCSqGSIb3
DQEBAQUAA4IBDwAwggEKAoIBAQCh5bQTShhS6nwlHuCEqLauSIilfI2ZU+XQDTSR
9/DJYjti4JLOwvEF0jFmQ+Rqv9dVP4YP5ElcsKt9R323hm7BamHjAokrqu6WrJEE
ge2SvHVdgMfevoNcr4i/Dbe2R5magija+rrMcBawmzk1M5662jtO/TeceMZ9m9Bd
YvmEsqSIGNx8XZU1u+gjrW+MrHXS/NOpbSq3oIBB72X15BXF8OeuXjPruZu3c3HY
qluKu7IFJt3QXEOiR7HmZ9wLp+hVuXEG0tBpQDeYW1JJ+VA3zVTJOZlZOQ1M9WBT
DsK4IFqPMV7djXAWyH5+FrznIHtngxjbPb0zD+/izAtvpY5DAgMBAAGgADANBgkq
hkiG9w0BAQUFAAOCAQEAGDJ6eniszawZXyK/e4LmBga5sF5Mtq/Zq5ProXdkakVG
XOrrGdb65xa4gq92gciPc4lmAF+5BdLO2bpuC1BmFZ/54xB60N59JnPFe5wUDRiA
QtE/G4luRAtq4aRUmwUQozAJzuPwgLUUQ5dM+wUgOlvYgGbgDvCMC/QEzGAyH1zy
Qj/ljMCXCVMLMmufTAk1Z1vktEnIG8u4Xc8KpdMw2C2SgTc3IdBmZaX8uQ/zDrPi
Pr98MrIodrE0U5NpXQS6P4NHZXDm/+WFMpvEkmzO7UCz27DX/WtFqQgvlWb9m5DU
Ihg8I9PUVw6O6Ag6h1D/lTrWMhTABfu3Ywvjocu6/Q==
-----END CERTIFICATE REQUEST-----Example Certificate (so that you can see the format, this is not actually useable):
-----BEGIN CERTIFICATE-----
MIICqDCCAZACCQDsX/Y+RSLBDjANBgkqhkiG9w0BAQUFADAWMRQwEgYDVQQDEwtk
b250LnVzZS5tZTAeFw0xMTEwMDEyMjQ5MzlaFw0xMTEwMDIyMjQ5MzlaMBYxFDAS
BgNVBAMTC2RvbnQudXNlLm1lMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKC
AQEAoeW0E0oYUup8JR7ghKi2rkiIpXyNmVPl0A00kffwyWI7YuCSzsLxBdIxZkPk
ar/XVT+GD+RJXLCrfUd9t4ZuwWph4wKJK6rulqyRBIHtkrx1XYDH3r6DXK+Ivw23
tkeZmoIo2vq6zHAWsJs5NTOeuto7Tv03nHjGfZvQXWL5hLKkiBjcfF2VNbvoI61v
jKx10vzTqW0qt6CAQe9l9eQVxfDnrl4z67mbt3Nx2KpbiruyBSbd0FxDokex5mfc
C6foVblxBtLQaUA3mFtSSflQN81UyTmZWTkNTPVgUw7CuCBajzFe3Y1wFsh+fha8
5yB7Z4MY2z29Mw/v4swLb6WOQwIDAQABMA0GCSqGSIb3DQEBBQUAA4IBAQBkAEUH
XffMxCttSDSzjC1Lnua7jXVUTWLXxxfJZQ/28QhS+n5nQZGYzyQGXEuCE7nVxEBZ
aJYlL5Yhdu+GJr36OIWFebvoZRrMOqukFpy5FfWxghjpPlAkw+M/VM54SACm9Mzk
w95OjpI/ogCWki94NQDdrKnA09tCXIdid5WzoFlrGhAgiIAyYuCUHAz5e44DCEu1
yLr5oUpsd7cdCe4U9iY5eHK7XUQPBuBQbZ/Nt580XCydpsEoleopsYPmn+WvXyOU
jT4mQP+b5hwQCtW7+KGtPbxhk0+9jOqP1gzwsAFPADO5MuBLvk5CwdNJ5awh8L/x
K4ZLP4tYYTJSL6rh
-----END CERTIFICATE-----