Automatic Assignment of Azure SSO Users to Groups
In LF appliance the users who are authenticated via a SSO/SAML2 service can be also assigned to a LF group automatically. Compare to the assignment of LDAP/AD users this needs bit more effort because we need first add a memberOf claim in the Azure application which will map the groups of users to the SAML response from where the LF server can filter groups them and assign users to a matching LF group.
Please note that opposite to LDAP/AD the existing users authenticated via a SSO/SAML2 service are not automatically re-assigned to other LF group if user's SSO groups have been changed in the Azure administration.
Setup MemberOf claim in Azure
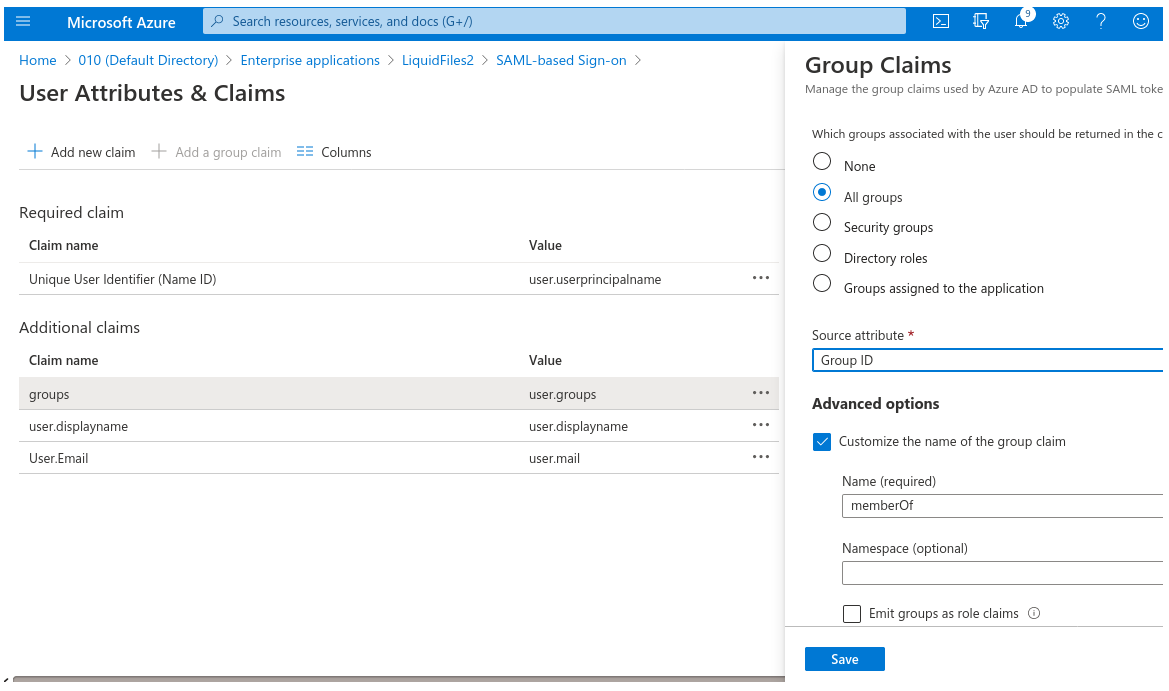
- In the Azure portal open Enterprise Applications, select the application in the list, select Single Sign On configuration, and then select User Attributes & Claims. Click on Add a group claim option.
- Define which type of groups associated with the user should be returned in the claim. You can select either Security groups or All groups or Groups assigned with the application (only if you have some groups associated with your LF SSO app).
- Optionally you can define a group filter to look up only in the groups where you have your LF users.
- Enable the Customize the name of the group claim checkbox and type memberOf in Name field.
- Make sure the Namespace field is empty and save the group claim settings.
In the SAML response should be returned now the memberOf claim with the user's group IDs. The SAML responses are listed in the debug logs in the Admin → Activity Log list.
APPLOG Debug: {"message":"SAML Response","saml_attributes":{"http://schemas.microsoft.com/identity/claims/tenantid":["..."],
"http://schemas.microsoft.com/identity/claims/objectidentifier":["..."],
"http://schemas.microsoft.com/identity/claims/identityprovider":["..."],
"http://schemas.microsoft.com/claims/authnmethodsreferences":["..."],
"user.displayname":["Joe Doe"],
"memberOf":["1defca82-7a1f-4c96-90a1-472e08031a2f"],
"name_id":"joe.doe@domain.com"},"user_id":"n/a","user_group":"n/a","resource":"session_saml_response","domain":"default","access_method":"HTML",
"ip":"...","hostname":"n/a","location":"Private","request_id":"...","log_level":"debug"}
Now in the Azure portal in the Groups settings is needed to find out all Group IDs you may need for automatic assignment of your LF users.
Note: In most of cases you will have to rely on only on the Group IDs. The group names can be used only with the Group assigned to the application option. The restriction to groups assigned to the application is because a group name is not unique, and display names can only be emitted for groups explicitly assigned to the application to reduce the security risks. Otherwise, any user could create a group with duplicate name and gain access in the application side.
Group Matching
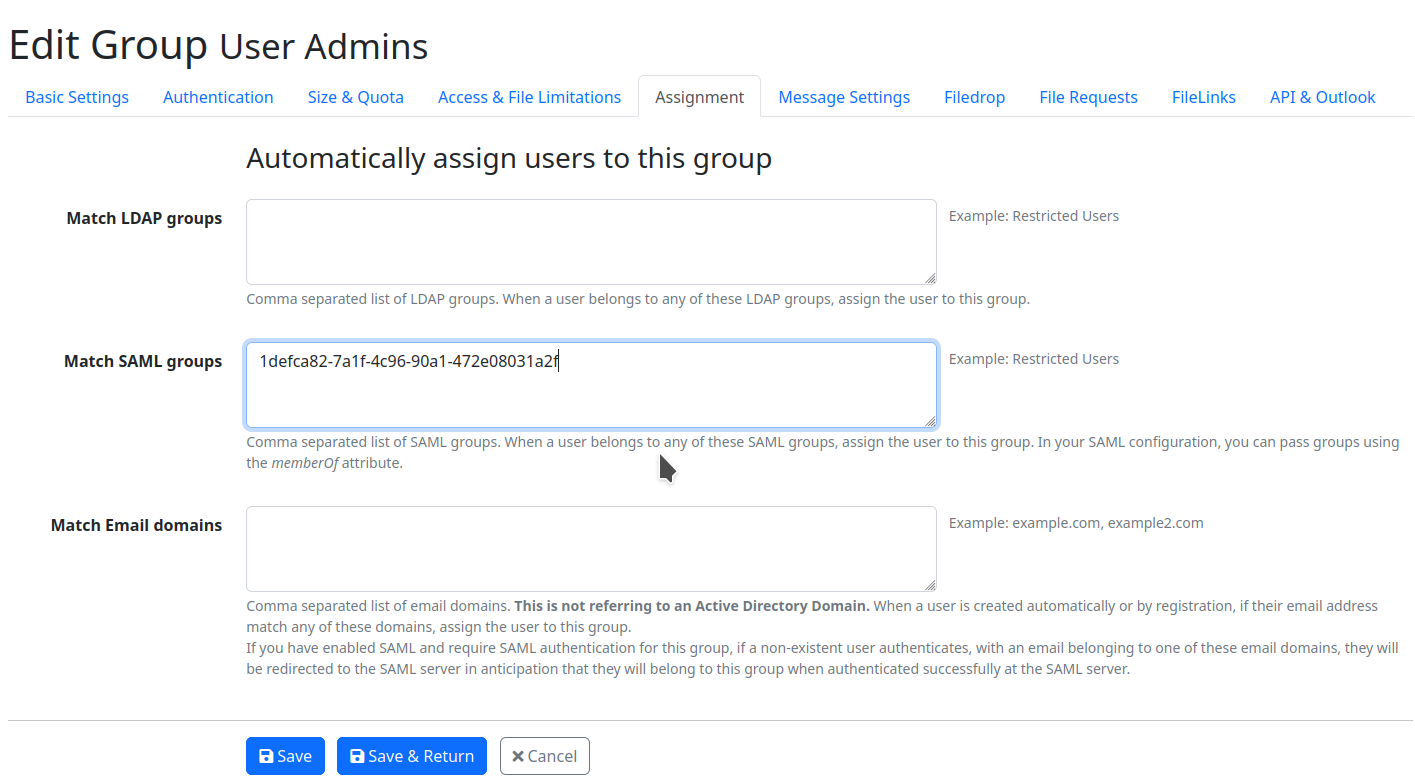
Finally on the LF server just put that group IDs in the LF groups,in the Match SAML groups fields, where the particular SSO users should be assigned to.
Example: Let's say you have some users which should administer users on the LF server and you need that these users should be assigned to the User Admins group on the LF server. This users are members of an Azure group represented with a Group ID: 1defca82-7a1f-4c96-90a1-472e08031a2f.
So it's needed to paste that GroupID in the Match SAML groups field, in the User Admin group under the Admin → Groups → edit user admins → Assignment tab.